Email Authentication – Key to Getting Your Emails Delivered

Updated February 2018
What’s the key to ensuring that your emails get delivered into your subscribers’ inboxes? Email authentication. In this article, we focus on the major email authentication standards—Sender Policy Framework (SPF), Sender ID, and DomainKeys Identified Mail (DKIM), and Domain Message Authentication Reporting & Conformance (DMARC). You’ll find out how they work and why they are an essential for getting optimal performance results from all your email campaigns.
When It Comes to Email, What Does “Authenticate” Mean?
If an email says it’s from a certain organization, how can you be sure it’s actually from that organization (i.e, not from someone else who doesn’t have permission for sending emails on behalf of that organization)? That’s basically what email authentication is all about—verifying that the domain used in the From address is under the control of the sender.
By employing email authentication protocols, Internet service providers (ISPs) help to protect your subscribers from phishing scams and spammers. Phishing scams involve sending email on behalf of someone without their permission to fool the recipients into giving out personal information (e.g., passwords, bank account and credit card numbers) with the intent of stealing money or spreading malicious software. And, it can be easy to spoof email because simply adding a well-known brand’s name and logo often will fool many email users.
When an ISP can’t authenticate a sender, the sender may face extra scrutiny that could lead to filtering. That means if your company has an authentication problem, your emails won’t make it into your subscribers’ inboxes. Instead, they will be identified as spam and likely land in the junk folders. In this way, email authentication is an important tool for marketers and a must for all legitimate organizations today because it directly impacts email deliverability.
How to Authenticate Email—Email Authentication Methods That Can Help Your Marketing Messages Reach Subscribers’ Inboxes
The following are the primary authentication methods used today. These authentication standards were designed to supplement the basic protocol used to send email—Simple Mail Transfer Protocol (SMTP)—because SMTP doesn’t have any authentication mechanisms.
-
Sender Policy Framework (SPF)
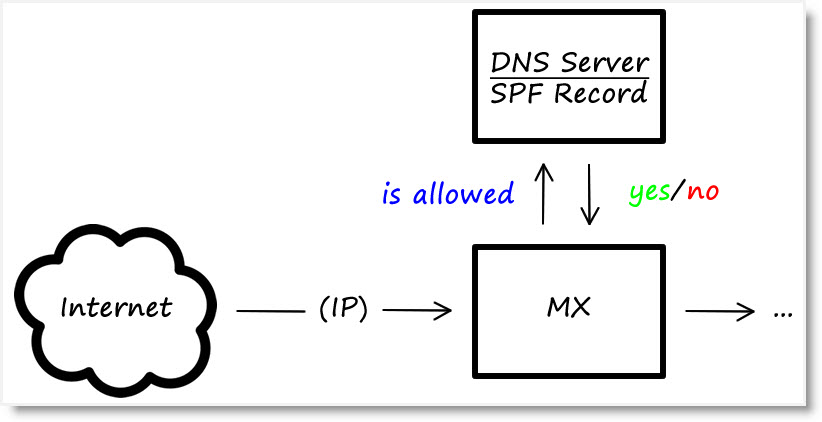
This authentication method verifies the envelope of the email, specifically the HELO identity (the mail server that is sending the message) and the MAIL FROM identity (the email address that is responsible for sending the message). So when your organization sends an email, your recipient’s mail server will evaluate your sending IP addresses in the public Domain Name System (DNS) to be sure it is allowed to send emails on behalf of the sender. AOL, Gmail, and many others are known to use SPF when checking authentication. For more information about SPF—including SPF record syntax details and a test suite for SPF implementation—visit the Sender Policy Framework Project Overview website. -
Sender ID
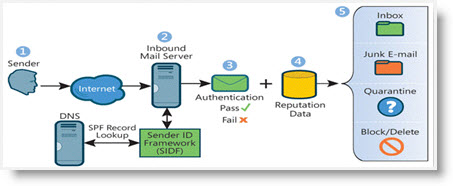
Similar to SPF, Sender ID verifies the email senders’ IP address against the alleged owner of the sending domain. The difference is that Sender ID uses an algorithm, called Purported Responsible Address (PRA), to examine the message content of email by specifically focusing on the From address your recipients see. Developed by Microsoft, Sender ID was not ultimately widely adopted, and, at this point, Microsoft took down their website relating to Sender ID. So, one can make the assumption that Sender ID is now obsolete, although it is still used by some ISPs. So, if you do set up Sender ID, you should ensure that it is set up correctly. For more information about the technical aspects of Sender ID, check out Unlock the Inbox. -
DomainKeys Identified Mail (DKIM)
With DKIM, two corresponding “keys” are created – one that is public, stored in the DNS as text, as well as a private key that is accessible just to the email server. So every time an email campaign is sent, a private key is included in the email message headers. When ISPs receive the email message in their servers, they can verify the public and private headers. This information is used to verify not only the sender, but also that the email message was not changed in transit. Yahoo, AOL and Gmail are known to use DKIM when checking authentication. In addition, Hotmail also uses DKIM, but typically only when Sender ID fails.For the DKIM authentication method, DomainKeys technology is combined with Identified Internet Mail (IIM). DomainKeys verifies the domain of the email sender by encrypting the email header and replacing it with a hash value. The receiving site also encrypts the email and compares the hash values to be sure they match. Using public key cryptography, email senders add a domain name and signature to their messages. The signature is verified at the receiving end by using the DNS. For more information about implementing DKIM, visit DKIM.org.
-
Domain Message Authentication Reporting & Conformance (DMARC)
The DMARC email-validation system is an email authentication, policy, and reporting protocol that is designed to identify spam and phishing messages and keep them out of people’s inboxes. It builds on the DKIM and SPF protocols, adding linkage to the From domain, published policies for how recipients handle authentication failures, as well as reporting from receivers to senders. DMARC protects both email senders and recipients by helping them streamline the process and work together to avoid costly abuse by spammers and phishers.Many of the email clients, such as Gmail, Yahoo, and Outlook, require that email messages are DMARC compliant. In addition, DMARC also helps to ensure that emails sent by spammers who are using a sender’s domain won’t hurt the domain’s overall reputation. That’s why adding a DMARC record for a domain—together with DKIM and SPF authentication—will help ensure your email deliverability.
For more information, visit the DMARC website.
Make Email Authentication Part of Your Email-Marketing Best Practices
Managing your authentication affects how your company’s emails are displayed in different email clients. If you haven’t authorized an email service provider (ESP) to send on behalf of your company, most major email clients will flag your emails in the From line as coming from a different server, which in turn, will cause the emails to be blocked or your recipients to think they’re getting spam.
In Outlook 2016, for example, if you haven’t authorized your ESP to send emails on behalf of your company, your email will display in the recipient’s inbox as being “sent by” someone else (e.g., the ESP’s mail server). Similarly, Outlook.com uses the phrase “on behalf of” and Gmail uses “via” to indicate that an email’s sending domain hasn’t been authenticated.
To get the best email deliverability rates, you should be implementing every email authentication standard available. Keep in mind that not all ISPs use the same email authentication tools.
If you’re looking for ways to improve your email deliverability – including evaluating and implementing email authentication standards – the experts at FulcrumTech can help. Email or give us a call at 215-489-9336 and get started today.
- Email Deliverability — What You Need to Know about Getting Your Emails to the Inbox
- Please Don’t Call It an Email Blast
- What You Need to Know About the CAN-SPAM Act
- How to Deal with Yahoo Email Delivery Issues
- 5 Ways to Improve Your Email Reputation and Delivery Rates
- The Best Email-Marketing Practices


